The AAA feature allows you to verify the identity of, grant access to, and track the actions of users managing C2000 Series switches. The C2000 Series switches support Remote Access Dial-In User Service (RADIUS) or Terminal Access Controller Access Control device Plus (TACACS+) protocols.
Based on the user ID and password combination that you provide, the C2000 Series switches perform local authentication or authorization using the local database or remote authentication or authorization using one or more AAA servers. A preshared secret key provides security for communication between the C2000 series switches and AAA servers. You can configure a common secret key for all AAA servers or for only a specific AAA server.
Fig 2.1.1 AAA C2000 Series Switches
AAA AUTHENTICATION
AAA security provides the following services:
1) Authentication - Identifies users, including login and password dialog, challenge and response, messaging support, and, encryption depending on the security protocol that you select. Authentication is the process of verifying the identity of the person or device accessing the C2000 Series switches. This process is based on the user ID and password combination provided by the entity trying to access the C2000 switch. The C2000 Series switches allow you to perform local authentication (using the local lookup database) or remote authentication (using one or more RADIUS or TACACS+ servers).
2) Authorization - Authorization Provides access controls.
AAA authorization is the process of assembling a set of attributes that describe what the user is authorized to perform. Authorization in C2000 Series switches is provided by attributes that are downloaded from AAA servers. Remote security servers, such as RADIUS and TACACS+, authorize users for specific rights by associating attribute-value (AV) pairs, which define those rights with the appropriate user.
3) Accounting - Provides the method for collecting information, logging the information locally, and sending the information to the AAA server for billing, auditing, and reporting.
The accounting feature tracks and maintains a log of every management session used to access the C2000 Series switches. You can use this information to generate reports for troubleshooting and auditing purposes. You can store accounting logs locally or send them to remote AAA servers.
Login authentication is used when user try to login into the switch. Such as CLI login dialog and WEBUI login web page. Enable authentication is used only on CLI for user trying to switch from User EXEC mode to Privileged EXEC mode.Both of them support following authenticate methods. TACACS+ provides more control over the authorization of commands while in RADIUS, no external authorization of commands is supported. All the AAA packets are encrypted in TACACS+ while only the passwords are encrypted in RADIUS is more secure.
Each list allows you to combine these methods with different orders. For example, we want to authenticate login user with remote TACACS+ server, but server may be crashed. Therefore, we need a backup plan, such as another Radius server. So we can configure the list with TACACS+ server as first authentication method and Radius server as second one.
Switch#configure terminal
Switch(config)# aaa authentication (login | enable) (default | listname ) [methodlist ][methodlist] [methodlist] [methodlist]
Switch(config)# no aaa authentication (login | enable) {listname}
|
Syntax |
aaa authentication (login | enable) (default | listname ) methodlist [methodlist] [methodlist] [methodlist] no aaa authentication (login | enable) {listname} |
|
Parameter |
login Add/Edit login authentication list |
|
enable Add/Edit enable authentication list |
|
|
default Edit default authentication list |
|
|
listname Specify the list name for authentication type |
|
|
methodlist Specify the authenticate method, including none, local enable, tacacs+, radius. |
|
|
Default |
Default authentication list name for type login is “default” and default method is “local”. Default authentication list name for type enable is “default” and default method is “enable” |
|
Mode |
Global Configuration |
|
Example |
This example shows how to add a login authentication list to authenticate with order tacacs+, radius, local. Switch(config)# aaa authentication login test1 tacacs+ radius local This example shows how to show existing login authentication lists Switch# show aaa authentication login lists Switch(config)# aaa authentication enable test1 tacacs+ radius enable This example shows how to show existing enable authentication lists Switch# show aaa authentication login lists Enable |
2.1 LOGIN AUTHENTICATION
Different access methods are allowed to bind different login authentication lists. Use “login authentication” command to bind the list to specific line (console, telnet, ssh).
Switch#configure terminal
Switch(config-line)# login authentication {listname}
Switch(config-line)# no login authentication
|
Syntax |
login authentication {listname} no login authentication |
|
Parameter |
listname Specify the login authentication list name to use. |
|
Default |
Default login authentication list for each line is “default”. |
|
Mode |
Line Configuration |
|
Example |
This example shows how to create a new login authentication list and bind to telnet line. Switch(config)# aaa authentication login test1 (tacacs+| radius | local | none |enable) Switch(config)# line telnet Switch(config-line)# login authentication test1 This example shows how to show line binding lists. Switch# show line lists |
2.2 IP HTTP LOGIN AUTHENTICATION
Different access methods are allowed to bind different login authentication lists. Use “ip (http | https) login authentication” command to bind the list to WEBUI access from http or https.
Switch#configure terminal
Switch(config)# ip (http | https) login authentication {listname}
Switch(config)# no ip (http | https) login authentication
|
Syntax |
ip (http | https) login authentication {listname} no ip (http | https) login authentication |
|
Parameter |
http: Bind login authentication list to user access WEBUI with http protocol https: Bind login authentication list to user access WEBUI with https protocol listname Specify the login authentication list name to use. |
|
Default |
Default login authentication list for each line is “default”. |
|
Mode |
Global Configuration |
|
Example |
This example shows how to create two new login authentication lists and bind to http and https. Switch#configure terminal Switch(config)# aaa authentication login test1 tacacs+ radius local Switch(config)# aaa authentication login test2 radius local Switch(config)# ip http login authentication test1 Switch(config)# ip https login authentication test2 This example shows how to show line binding lists. Switch# show line lists |
2.3 ENABLE AUTHENTICATION
Different access methods are allowed to bind different enable authentication lists. Use “enable authentication” command to bind the list to specific line (console, telnet, ssh).
Switch#configure terminal
Switch(config-line)# enable authentication {listname}
Switch(config-line)# no enable authentication
|
Syntax |
enable authentication {listname} no enable authentication |
|
Parameter |
listname Specify the enable authentication list name to use. |
|
Default |
Default enable authentication list for each line is “default”. |
|
Mode |
Line Configuration |
|
Example |
This example shows how to create a new enable authentication list and bind to telnet line. Switch#configure terminal Switch(config)# aaa authentication enable test1 tacacs+ radius enable Switch(config)# line telnet Switch(config-line)# enable authentication test1 |
2.4 SHOW AAA AUTHENTICATION
Use “show aaa authentication” command to show login authentication or Enable authentication method lists.
Switch#show aaa authentication (login | enable) lists
|
Syntax |
show aaa authentication (login | enable) lists |
|
Parameter |
login Show login authentication list. enable Show enable authentication list. |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show existing login authentication lists. Switch# show aaa authentication login lists Switch# show aaa authentication login lists |
2.5 SHOW LINE LISTS
Use “show line lists” command to show all lines binding list of all.
Switch#show line lists
|
Syntax |
show line lists |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show line binding lists. Switch# show line lists |
2.6 TACACS DEFAULT-CONFIG
Use “tacacs default-config” command to modify default values of tacacs+ server. These default values will be used when user try to create a new tacacs+ server and not assigned these values.
Switch#configure terminal
Switch(config)#tacacs default-config [key TACACSKEY] [timeout <1-30>]
|
Syntax |
tacacs default-config [key TACACSKEY] [timeout <1-30>] |
|
Parameter |
key TACACSKEY Specify default tacacs+ server key string. timeout<1-30> Specify default tacacs+ server timeout value. |
|
Default |
Default tacacs+ key is “********”. Default tacacs+ timeout is 5 seconds. |
|
Mode |
Global Configuration |
|
Example |
This example shows how modify default tacacs+ configuration Switch#configure terminal Switch(config)# tacacs default-config timeout 20 Switch(config)# tacacs default-config key tackey This example shows how to show default tacacs+ configurations. Switch# show tacacs default-config |
2.7 TACACS HOST
Use “TACACS+ host” command to add or edit tacacs+ server for Authentication, Authorization or accounting. Use “no” form to delete one or all TACACS+ servers from database.
Switch#configure terminal
Switch(config)# tacacs host {HOSTNAME }[port <0-65535>] [key TACPLUSKEY] [priority<0-65535>][timeout <1-30>]
Switch(config)#no tacacs [host {HOSTNAME }]
|
Syntax |
tacacs host HOSTNAME [port <0-65535>] [key TACPLUSKEY] [priority<0-65535>] [timeout <1-30>] no tacacs [host {HOSTNAME }] |
|
Parameter |
HOSTNAME Specify tacacs+ server host name, both IP address and domain name are available. port <0-65535> Specify tacacs+ server udp port key TACPLUSKEY Specify tacacs+ server key string priority <0-65535> Specify tacacs+ server priority timeout <1-30> Specify tacacs+ server timeout value |
|
Default |
Default tacacs+ key is “********”. Default tacacs+ timeout is 5 seconds. |
|
Mode |
Global Configuration |
|
Example |
This example shows command execution, |
2.8 SHOW TACACS DEFAULT-CONFIG
Use “show tacacs default-config” command to show tacacs+ default.
Switch#show tacacs default-config
|
Syntax |
show tacacs default-config |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show default tacacs+ configurations. Switch# show tacacs default-config |
2.9 SHOW TACACS
Use “show tacacs” command to show existing tacacs+ servers.
Switch#show tacacs
|
Syntax |
show tacacs |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show existing tacacs+ server. Switch# show tacacs |
2.10 SHOW Default-config
Use “radius default-config” command to modify default values of radius server. These default values will be used when user try to create a new radius server and not assigned these values.
Switch#configure terminal
Switch(config)#radius default-config [key RADIUSKEY] [retransmit <1-10>] [timeout <1-30>]
|
Syntax |
radius default-config [key RADIUSKEY] [retransmit <1-10>] [timeout <1-30>] |
|
Parameter |
key RADIUSKEY Specify default radius server key string retransmit <1-10> Specify default radius server retransmit value timeout <1-30> Specify default radius server timeout value |
|
Default |
Default radius key is “********”. Default radius retransmit is 3 times. Default radius timeout is 3 seconds |
|
Mode |
Global Configuration |
|
Example |
This example shows how modify default radius configuration, Switch#configure terminal Switch(config)# radius default-config timeout 20 Switch(config)# radius default-config key radiuskey Switch(config)# radius default-config retransmit 5 This example shows how to show default radius configurations. Switch# show radius default-config |
2.11 RADIUS HOST
Use “radius host” command to add or edit an existing radius server. Use “no” form to delete one or all radius servers from database.
Switch#configure terminal
Switch(config)# radius host {HOSTNAME } [auth-port <0-65535>] [key RADIUSKEY][priority <0-65535>] [retransmit <1-10>] [timeout <1-30>] [type (login|802.1x|all)]
Switch(config)# no radius [host {HOSTNAME }]
|
Syntax |
radius host HOSTNAME [auth-port <0-65535>] [key RADIUSKEY][priority <0-65535>] [retransmit <1-10>] [timeout <1-30>] [type (login|802.1x|all)] no radius [host HOSTNAME] |
|
Parameter |
HOSTNAMESpecify radius server host name, both IP address and domain name are available. auth-port <0-65535> Specify radius server udp port key RADIUSKEY Specify radius server key string priority <0-65535>Specify radius server priority retransmit <1-10> Specify radius server retransmit times timeout <1-30> Specify radius server timeout value |
|
Default |
Default radius timeout is 3 seconds. |
|
Mode |
Global Configuration |
|
Example |
This example shows how to create a new radius server Switch(config)# radius host 192.168.1.111 auth-port 12345 key radiuskey priority100 retransmit 5 timeout 10 type all This example shows how to show existing radius server. Switch# show radius |
2.12 SHOW RADIUS Default-config
Use “show radius default-config” command to show radius default configurations.
Switch#show radius default-config
|
Syntax |
show radius default-config |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show default radius configurations. Switch# show radius default-config |
2.13 SHOW RADIUS
Use “show radius” command to show existing radius servers.
Switch#show radius
|
Syntax |
show radius |
|
Mode |
Privileged EXEC |
|
Example |
This example shows how to show existing radius server. Switch# show radius 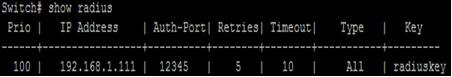
|